EasyAccess ZTNA
Secure Access, Zero Trust
Enterprise-grade Zero Trust Network Access that replaces legacy VPNs. Self-hosted for complete data sovereignty. 30+ device posture checks, built-in DLP, WAF, and CVE scanner — all included, no add-ons.
Why Legacy Security Fails
Traditional VPNs and VDI solutions were designed for a different era. Today's distributed workforce, BYOD policies, and sophisticated threats demand a fundamentally different approach to secure access.
VPN vulnerabilities are a primary attack vector. In 2024 alone, critical zero-day exploits hit Ivanti, Fortinet, SonicWall, and Check Point VPNs. Once attackers breach a VPN, they gain network-level access enabling lateral movement across your entire infrastructure.
Insider threats cost organizations $17.4M annually on average, with 83% of organizations experiencing at least one insider incident. Traditional perimeter security offers no protection against authorized users who misuse their access or have their credentials compromised.
VDI creates friction and costs. Latency of 100-300ms makes real-time collaboration impossible. At $500-2,000 per user annually, VDI infrastructure costs balloon while users struggle with non-native experiences and peripheral integration issues.
VPN: Network-Level Access
Once authenticated, users have broad network access. A single breach enables lateral movement across your entire infrastructure. No continuous verification.
VDI: Latency & Cost
100-300ms latency kills productivity. $500-2,000/user/year infrastructure costs. Non-native experience frustrates users. Complex capacity planning.
Insider Threats: $17.4M/Year
83% of organizations experience insider incidents. 81 days average containment time. Customer data in 42% of incidents, IP in 31%.
See EasyAccess in Action
Modern, intuitive interface for security teams and end users alike.
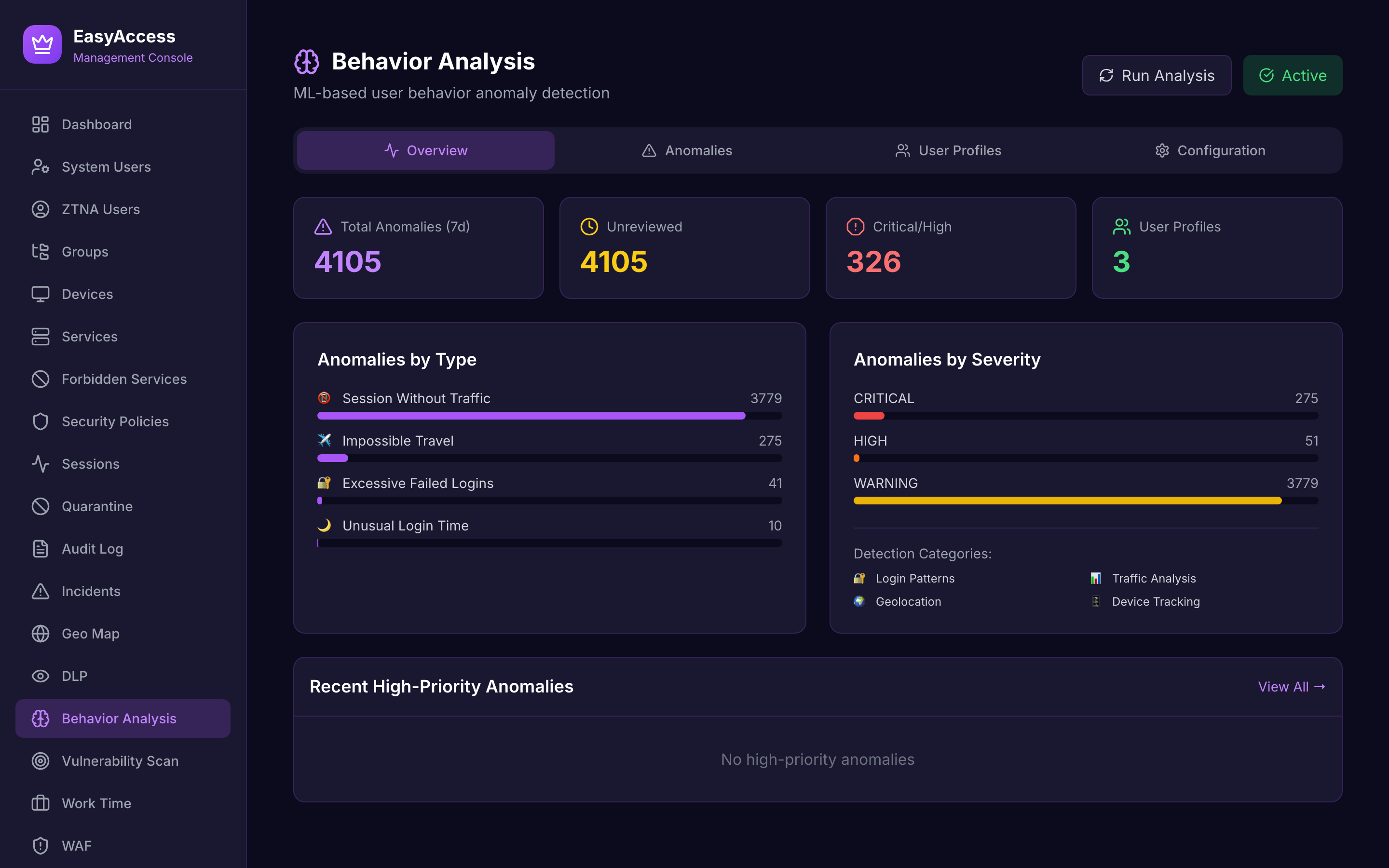
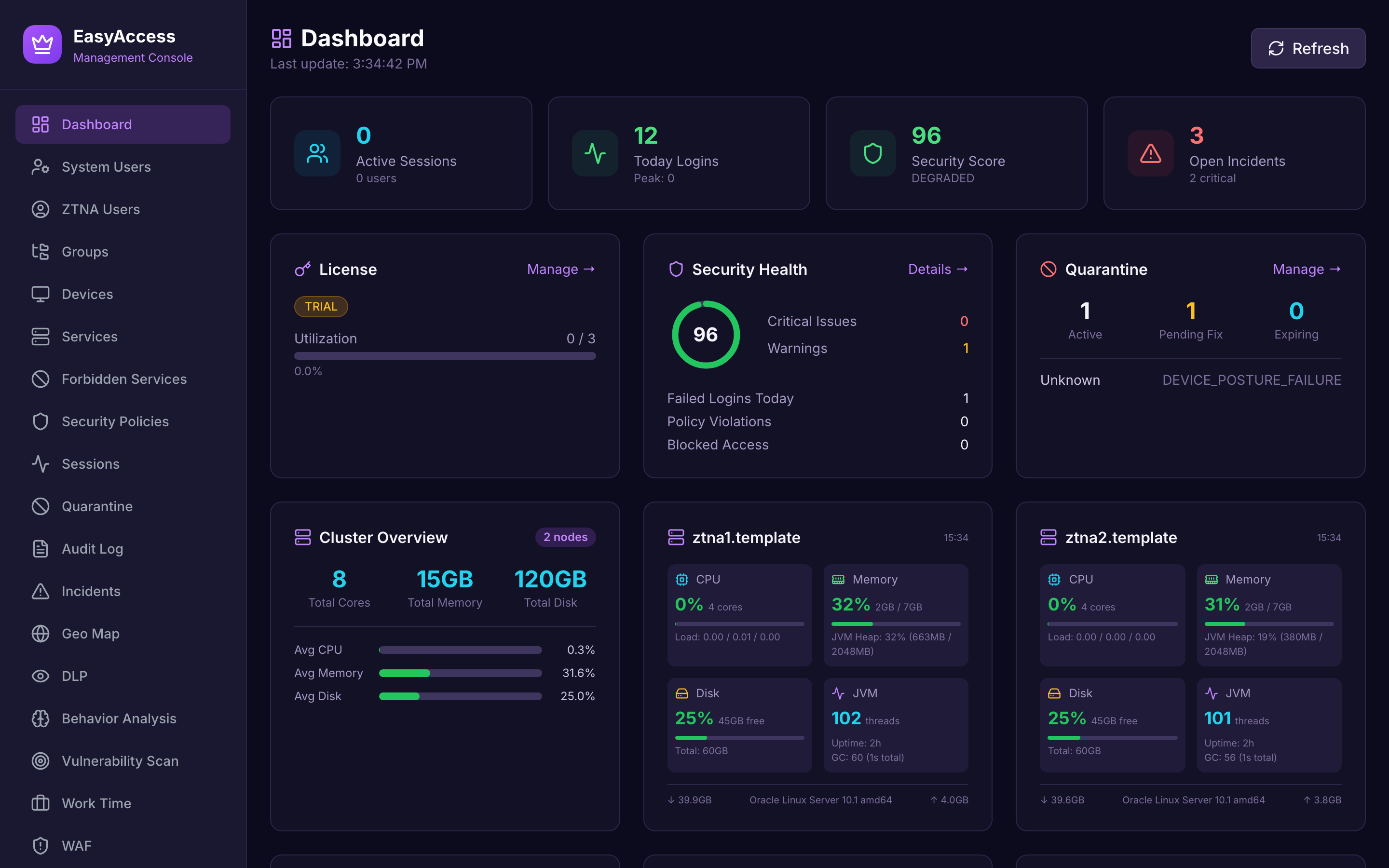
Management Dashboard
Real-time visibility into your Zero Trust infrastructure — active sessions, security health, incidents, and license utilization at a glance.
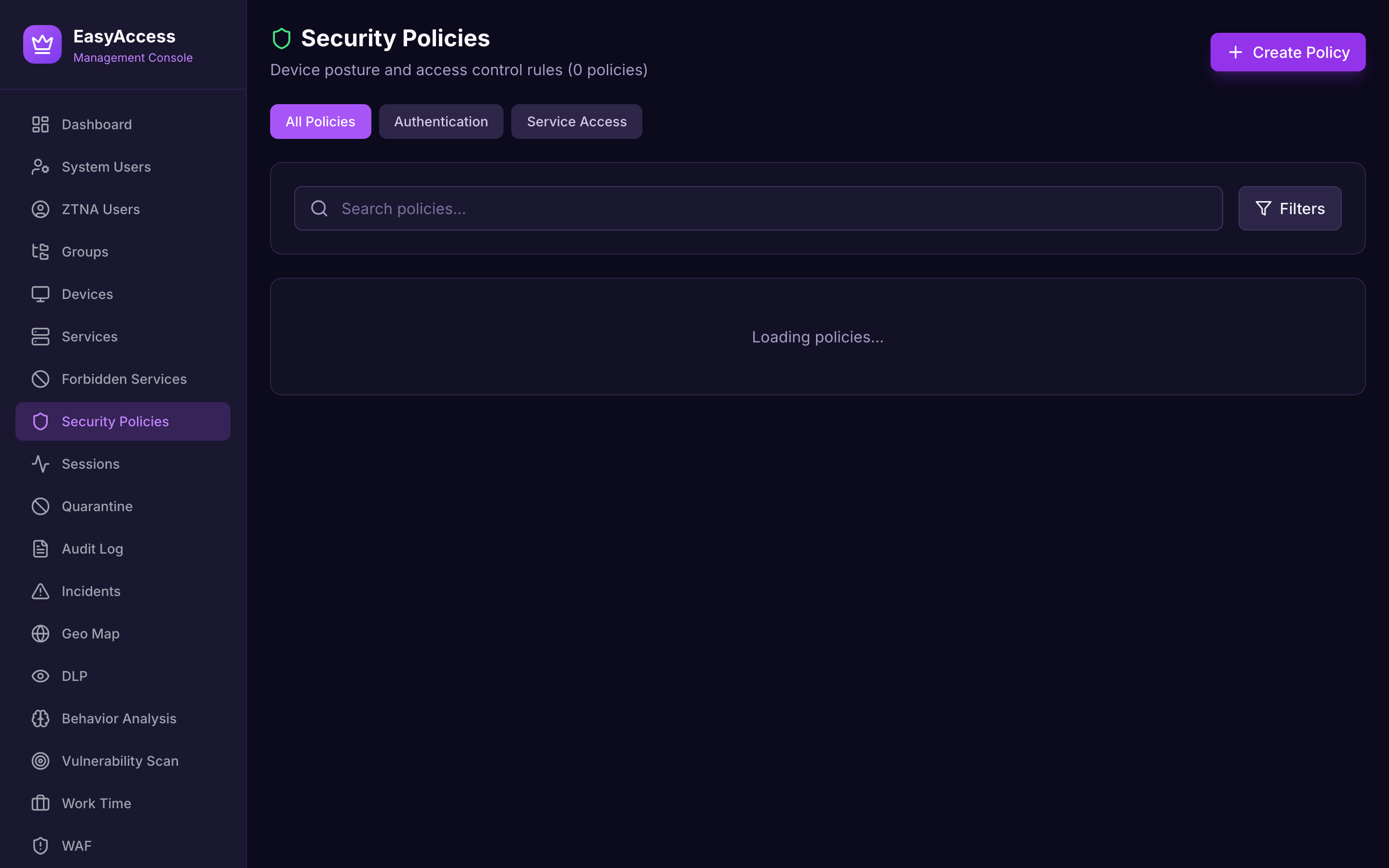
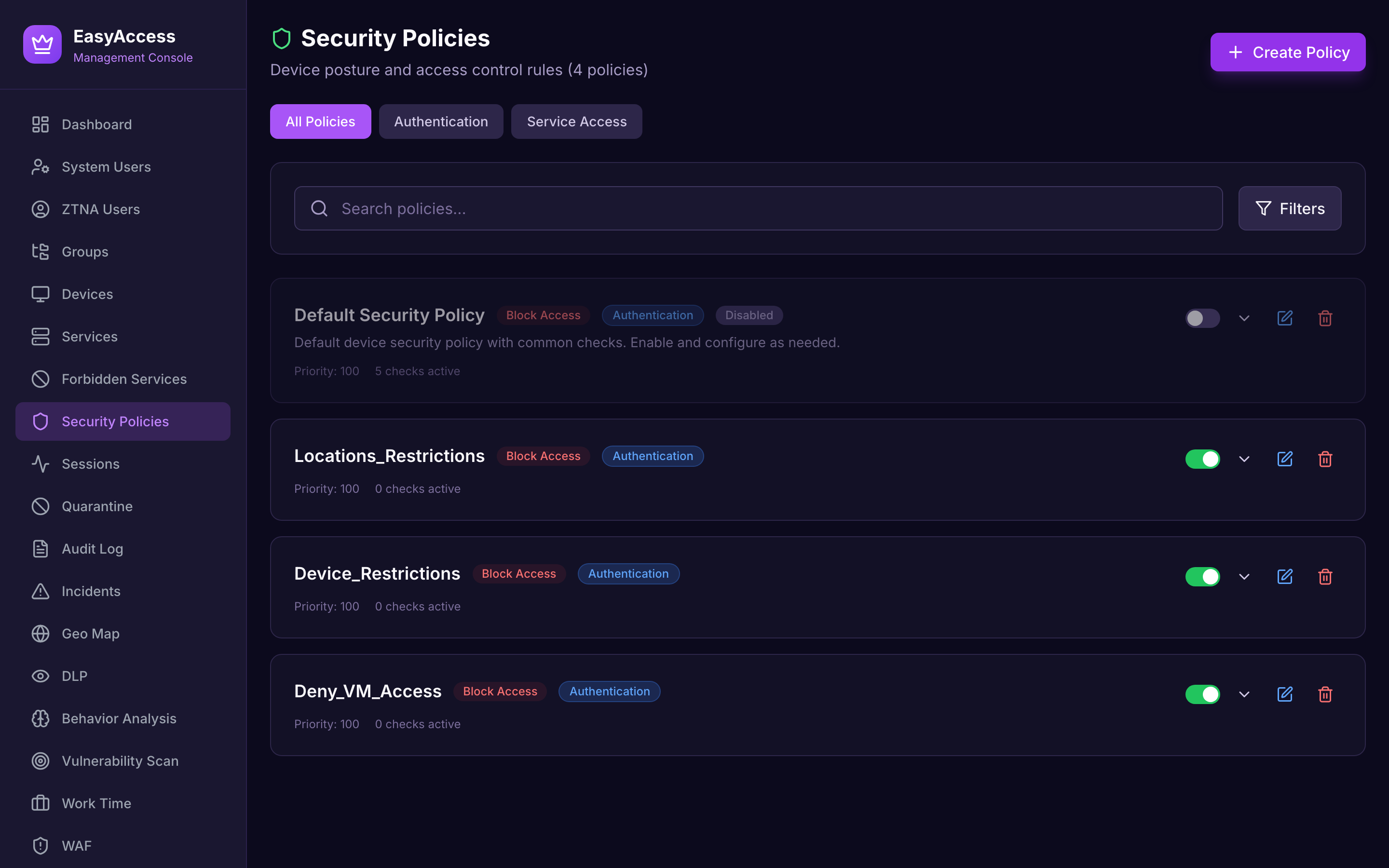
Security Policies
Configure granular access policies with device posture requirements, geographic restrictions, and time-based rules.
Security Health Center
Server-side security monitoring with SELinux, firewall, NTP, and cluster health checks.
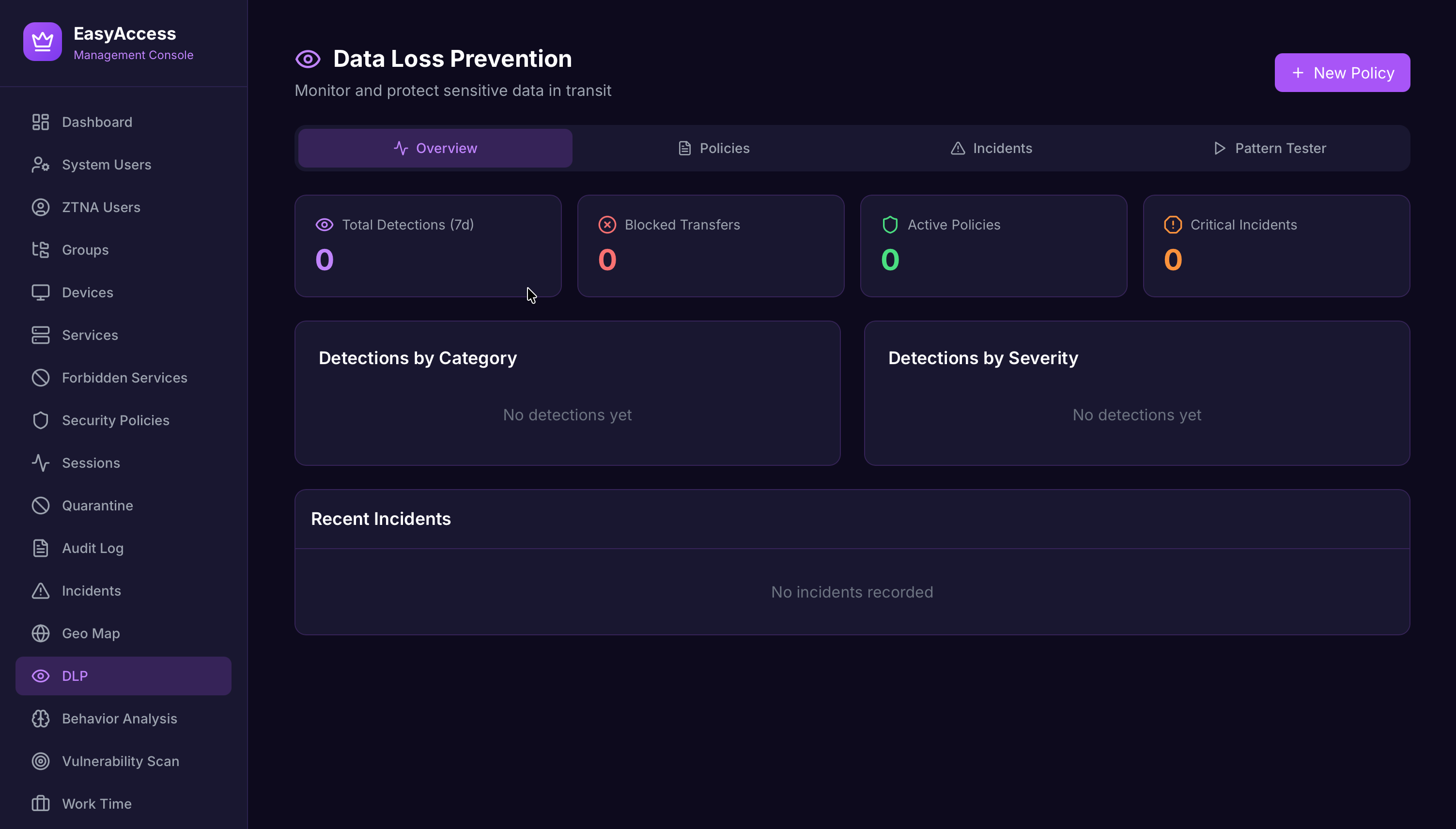
Data Loss Prevention
Real-time DLP with pattern detection for credit cards, SSN, and custom regex rules.
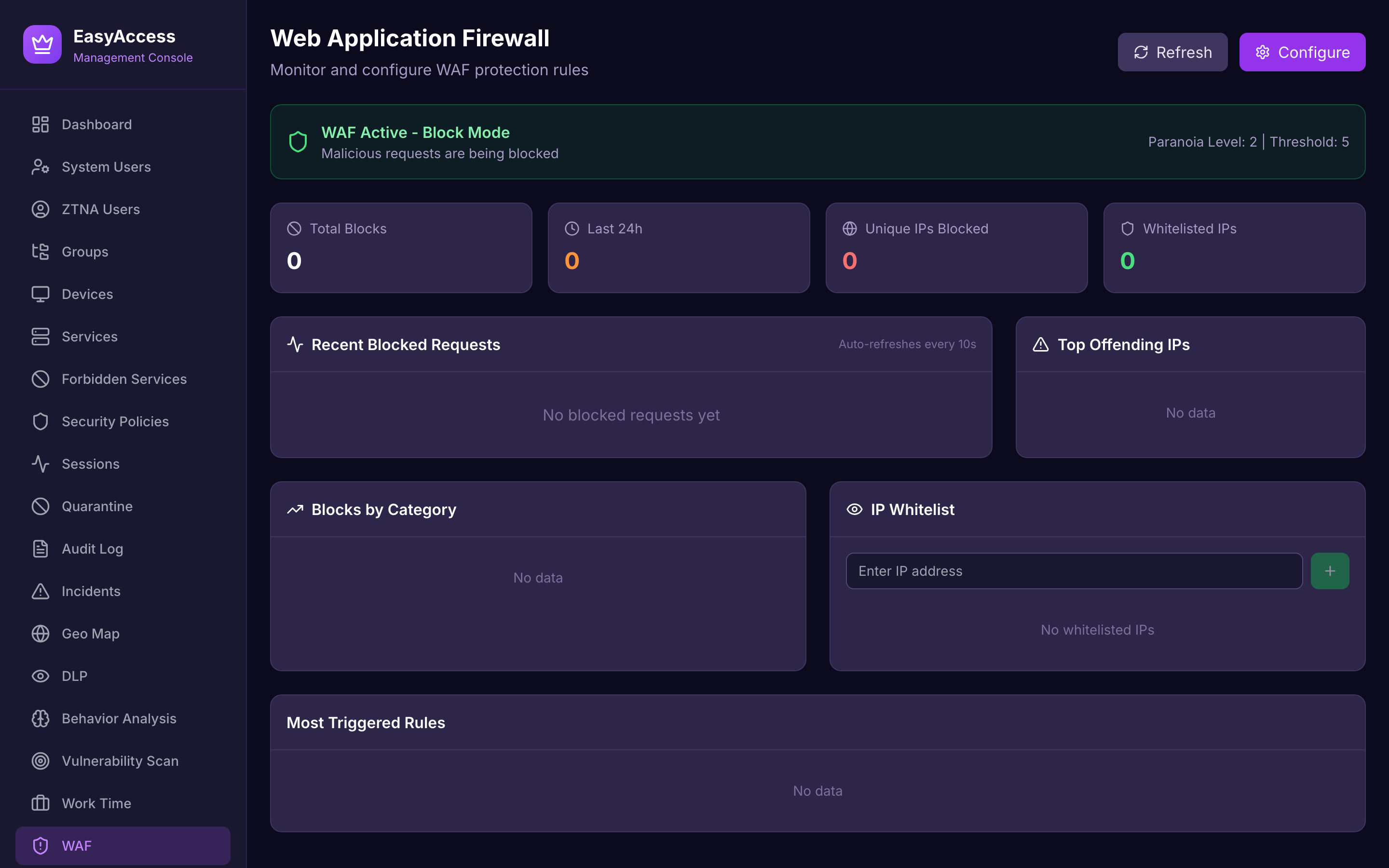
Web Application Firewall
OWASP Top 10 protection with SQL injection, XSS, and command injection blocking.
Behavior Analysis
ML-based anomaly detection for session patterns, geographic analysis, and risk scoring.
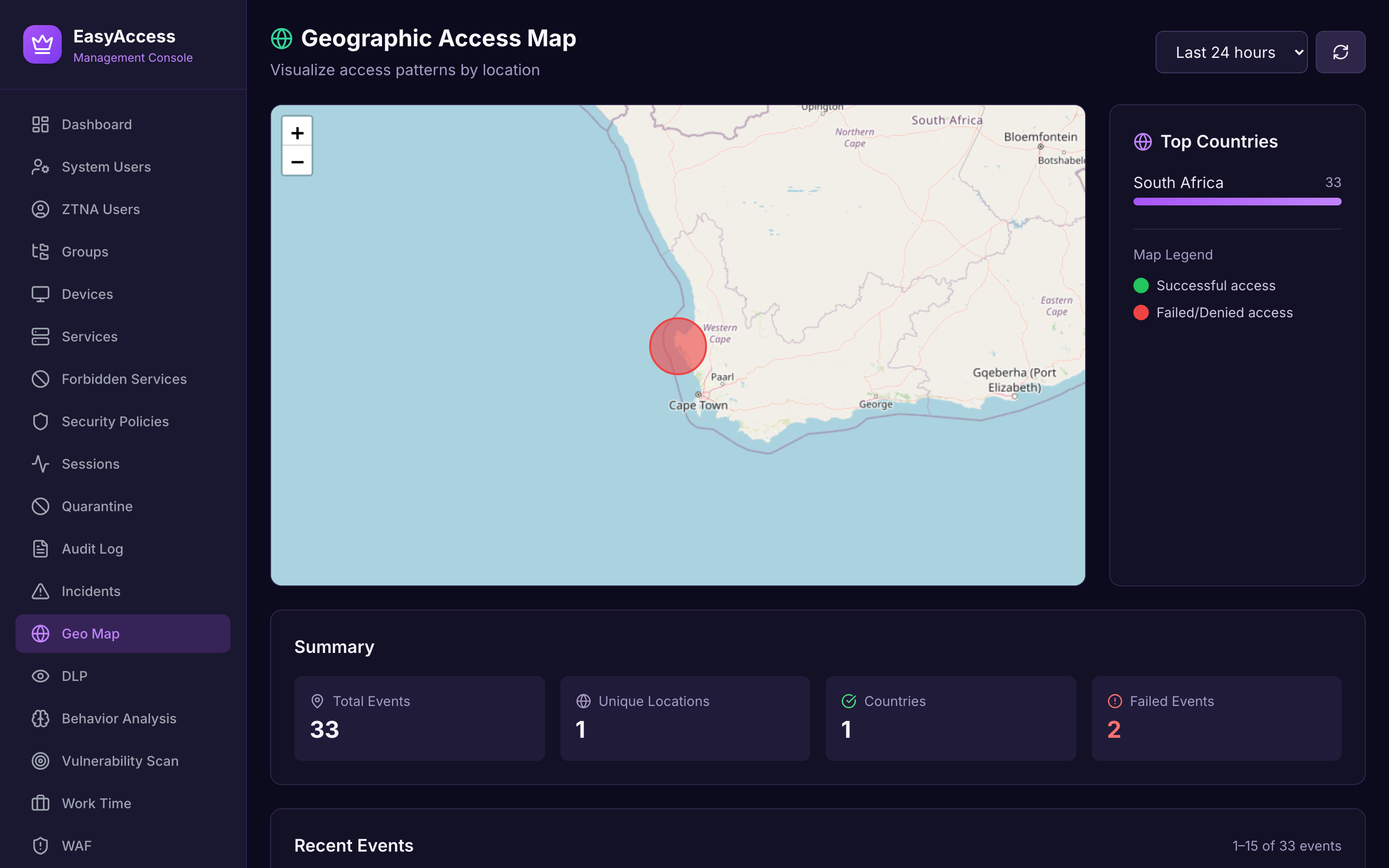
Geographic Monitoring
Visual connection map with GeoIP data and impossible travel detection.
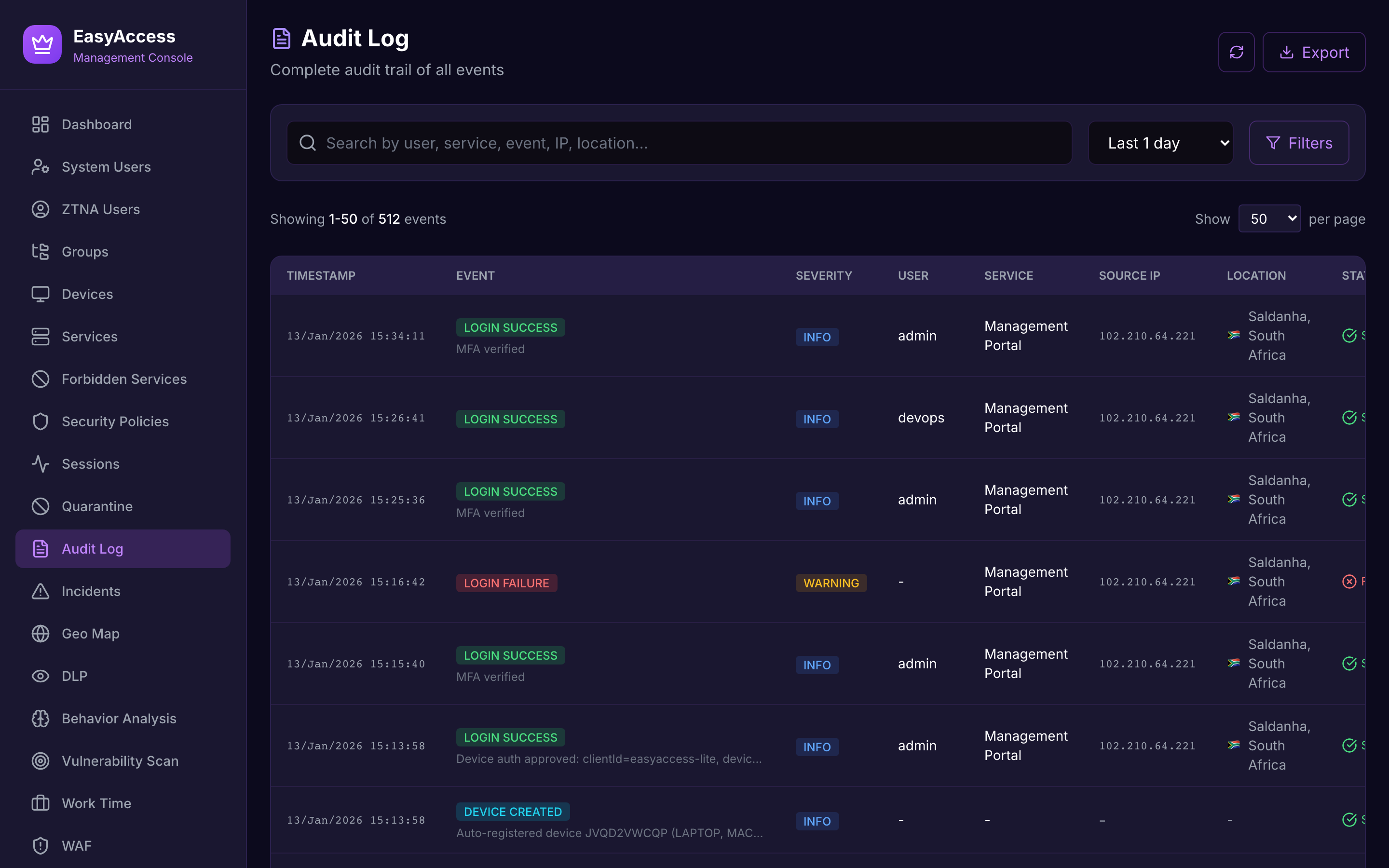
Audit Log
Complete activity tracking for compliance.
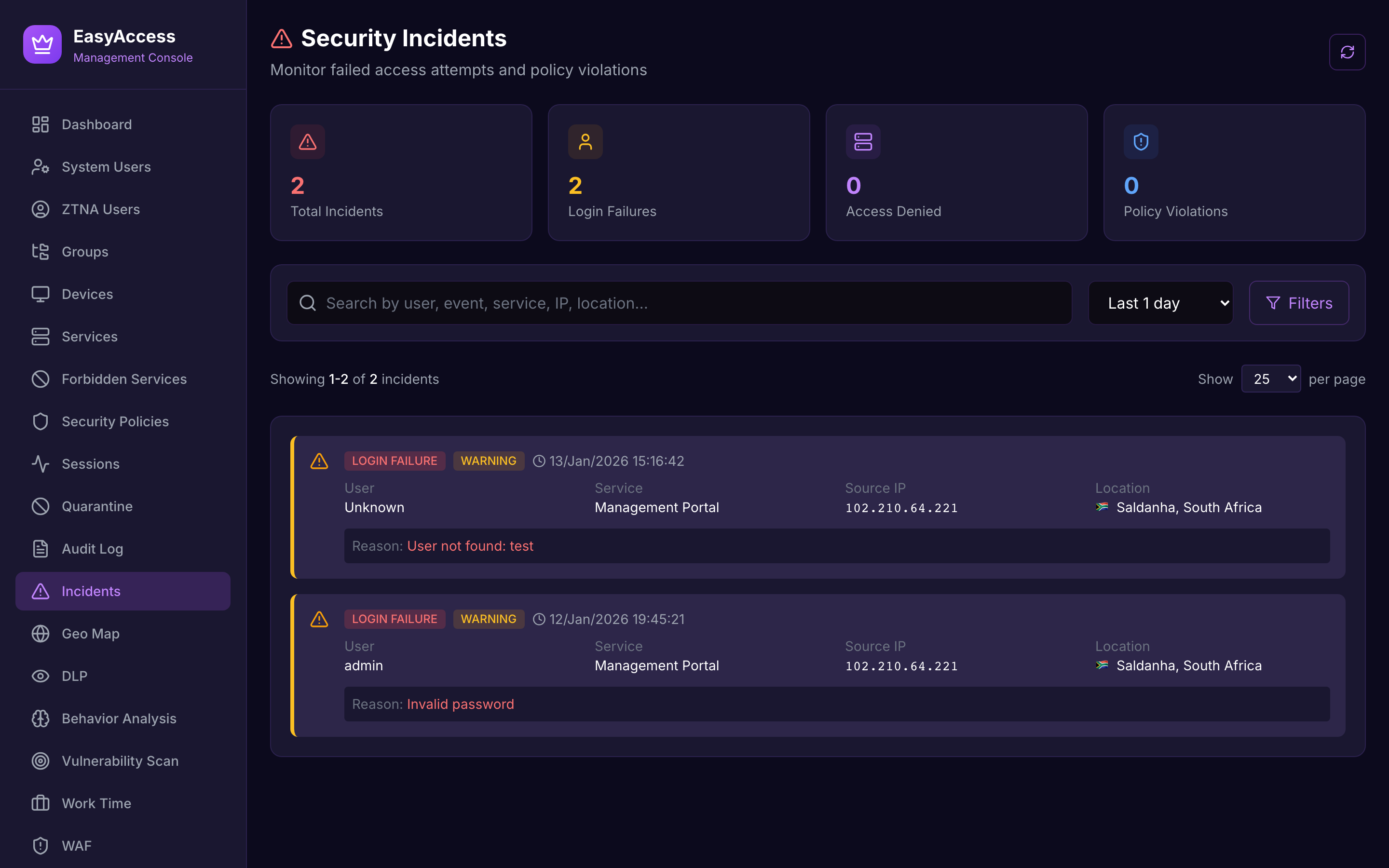
Incidents
Security events with severity and remediation.
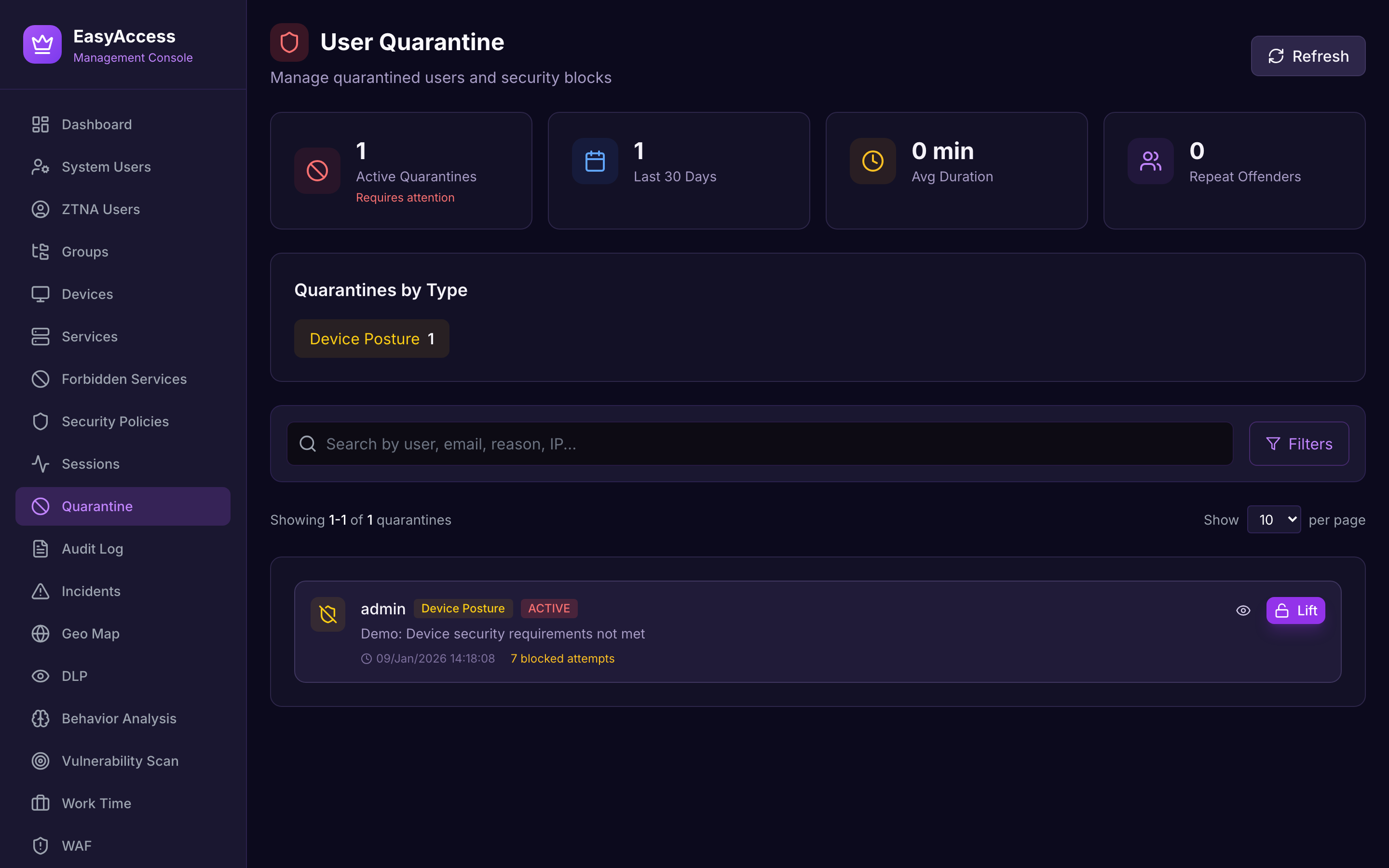
User Quarantine
Automatic isolation for policy violations.
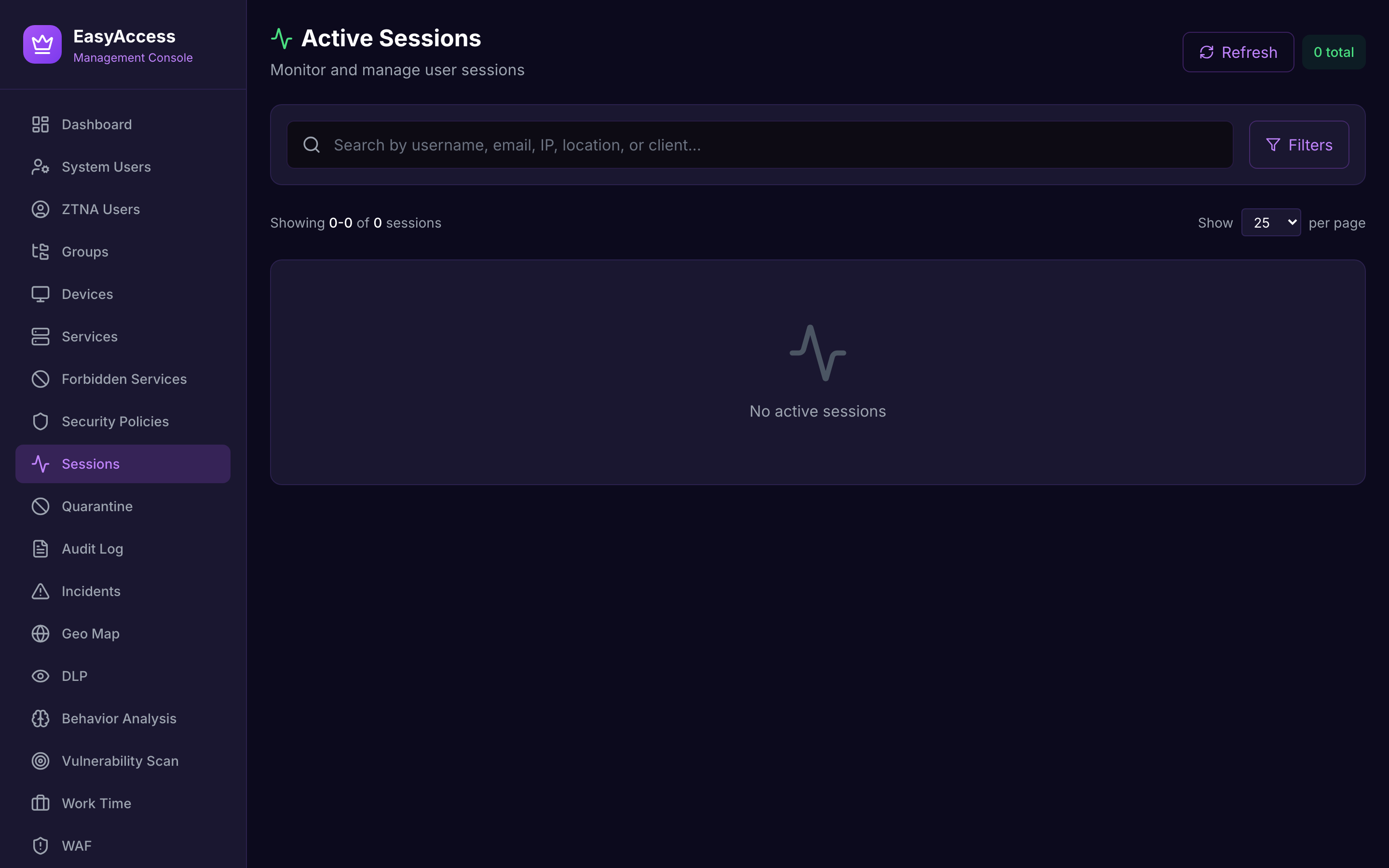
Active Sessions
Real-time session monitoring and control.
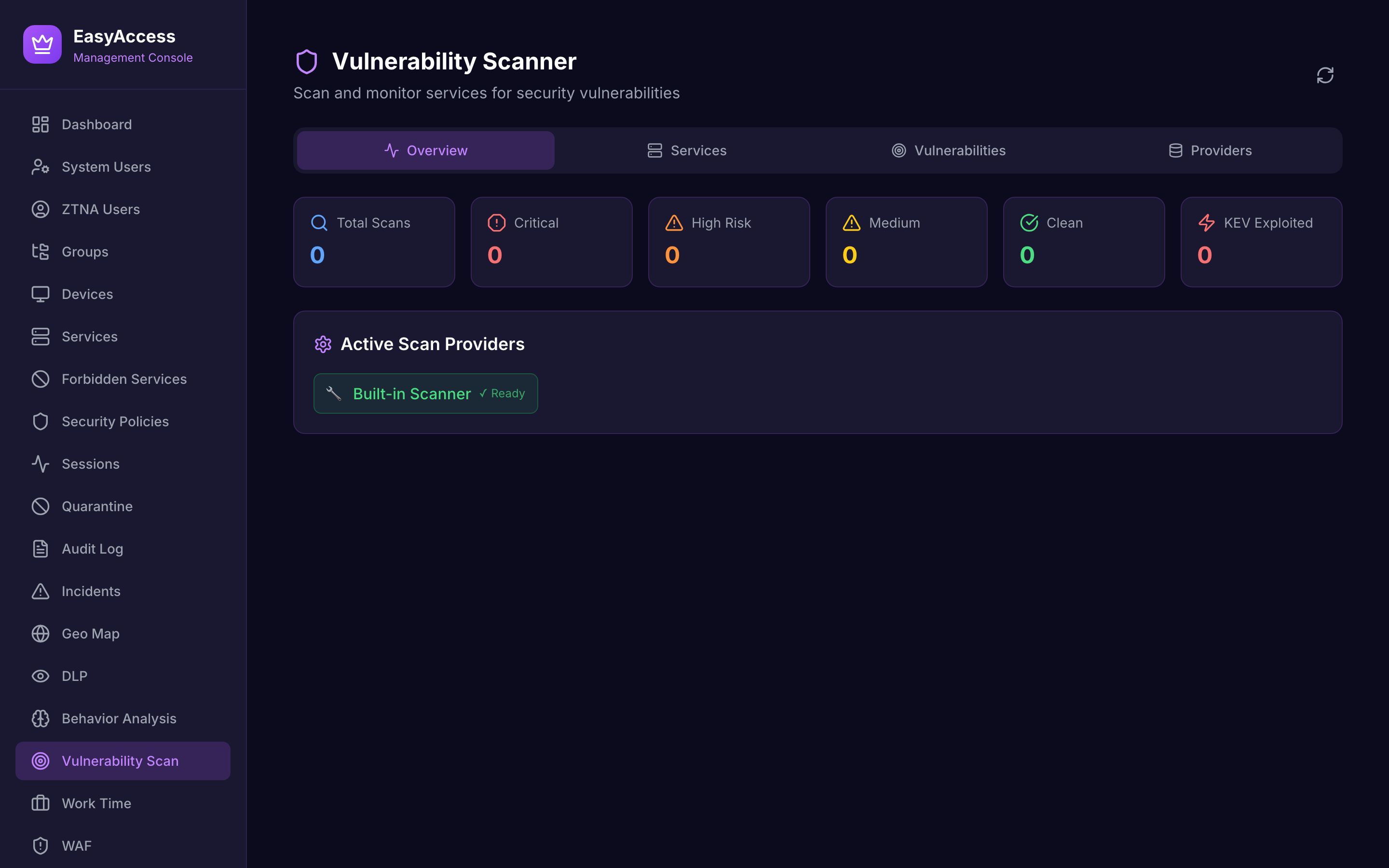
Vulnerability Scanner
CVE scanning with CVSS scoring.
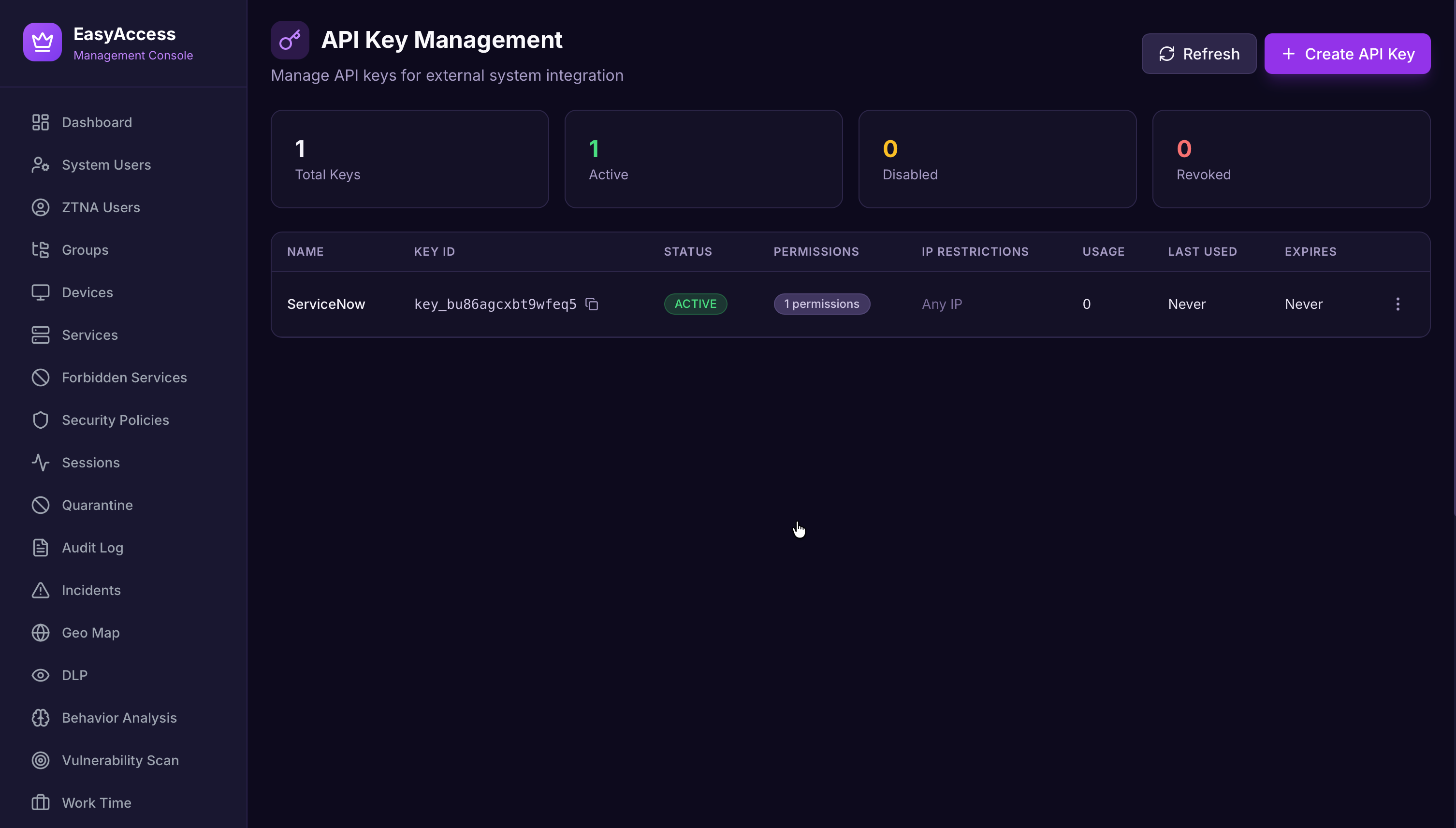
API Keys
Scoped API access for automation.
"Zero Trust means never trust, always verify. EasyAccess ZTNA enforces per-application access with continuous device posture verification — eliminating the implicit trust that makes VPNs vulnerable."
EasyAccess ZTNA provides application-level access rather than network-level access. Each service has its own security policy. Device posture is continuously verified. And everything runs on your infrastructure — complete data sovereignty.
Self-Hosted
Deploy on your infrastructure — on-premises, private cloud, or air-gapped environments. No data leaves your control. Full compliance with data residency requirements.
30+ Device Checks
Firewall, disk encryption, antivirus, OS version, TPM, Secure Boot, jailbreak detection, Wi-Fi security, machine certificates, process blacklist, NAT/router detection.
All-In-One Security
DLP with custom patterns, WAF with OWASP protection, CVE vulnerability scanner, behavior analysis with ML — all included. No expensive add-ons like competitors.
Multi-Platform Client
CLI for automation, GUI desktop app, browser extension for web apps. macOS, Windows, Linux. QUIC tunnels for low latency with WebSocket fallback.
Complete Security Platform
Everything you need to secure remote access, protect data, and maintain compliance — in a single self-hosted solution.
Device Posture Verification
Comprehensive endpoint security assessment with 30+ checks performed continuously during sessions, not just at login.
- Firewall & Disk Encryption status
- Antivirus presence & updates
- OS version & security patches
- TPM & Secure Boot verification
- Jailbreak/Root detection
- Wi-Fi security & machine certificates
- Process blacklist enforcement
- NAT/Router detection & TTL checks
Data Loss Prevention (DLP)
Real-time traffic inspection to prevent unauthorized data exfiltration through ZTNA tunnels.
- Credit card & PCI data detection
- SSN, passport, ID patterns
- Custom regex rules
- Block, warn, or log actions
- Template library for PII
- Severity-based alerts
- Detailed incident reports
- GDPR/HIPAA compliance support
Web Application Firewall
Protect applications from OWASP Top 10 and other web-based attacks with built-in WAF.
- SQL injection prevention
- Cross-site scripting (XSS) blocking
- Path traversal protection
- Command injection defense
- Custom rule definitions
- Request/response inspection
- Attack logging & analytics
- Real-time threat dashboard
Behavior Analysis
ML-based anomaly detection identifies unusual patterns and automatically responds to threats.
- Session frequency monitoring
- Connection time analysis
- Geographic pattern detection
- Impossible travel alerts
- Traffic volume baselines
- Automatic risk scoring
- Auto-quarantine triggers
- SIEM integration
Vulnerability Scanner
Scan protected services for known CVE vulnerabilities before attackers find them.
- NVD database integration
- CVSS severity scoring
- Scheduled automated scans
- Prioritized remediation
- Service-specific reports
- Trend tracking over time
- Alert notifications
- Executive dashboards
Identity & Access
Enterprise identity integration with SSO, MFA, and automated provisioning.
- SAML 2.0 & OAuth 2.0/OIDC
- SCIM 2.0 provisioning
- TOTP & WebAuthn MFA
- User & group management
- Role-based access control
- Session management
- User quarantine
- API key management
Enterprise Use Cases
EasyAccess ZTNA addresses security challenges across regulated industries with sensitive data requirements.
FinTech & Banking
Secure access to trading systems, customer financial data, and banking infrastructure. Meet PCI DSS, SOX, and SWIFT CSP requirements with comprehensive audit trails and data protection controls. Behavior analysis detects insider trading patterns.
Retail & E-Commerce
Protect customer PII, payment card data, and inventory systems across distributed store locations. DLP prevents credit card data exfiltration. Per-store access policies with seasonal contractor scaling. $3.48M average breach cost avoided.
Humanitarian Organizations
Protect beneficiary personal data, biometric identifiers, and location information for vulnerable populations. Self-hosted deployment ensures no cloud dependency in hostile environments. GeoIP restrictions prevent unauthorized access from certain regions.
Healthcare & Life Sciences
HIPAA-compliant access to EHR systems, medical devices, and patient data. Device posture verification ensures only secured endpoints access PHI. DLP prevents unauthorized patient data disclosure.
Government & Defense
Air-gapped deployments for classified systems. NIST 800-53 control implementation. Zero Trust architecture for contractor access management. Complete data sovereignty with on-premises deployment.
Technology & SaaS
Developer access to production infrastructure with per-service policies. CI/CD pipeline security. API key management with scoped permissions. Vulnerability scanner identifies security issues before deployment.
EasyAccess vs. Competitors
See how EasyAccess ZTNA compares to leading ZTNA vendors.
| Feature | EasyAccess | Zscaler ZPA | Palo Alto Prisma | Fortinet ZTNA |
|---|---|---|---|---|
| Deployment | Self-hosted / Cloud | Cloud only | Cloud only | Hybrid |
| Data Sovereignty | ✓ Full control | ✗ Cloud-hosted | ✗ Cloud-hosted | ~ Partial |
| DLP Built-in | ✓ Included | $ Add-on | $ Add-on | $ Add-on |
| WAF Built-in | ✓ Included | $ Add-on | $ Add-on | ✓ Yes |
| CVE Scanner | ✓ Included | ✗ No | $ Add-on | $ Add-on |
| Air-Gapped Deploy | ✓ Supported | ✗ No | ✗ No | ~ Limited |
| Entry Pricing | $ | $$$ | $$$ | $$ |
Ready to Replace Your VPN?
Request a demo to see EasyAccess ZTNA in action. Or start with our free trial — 3 users included with all features, no credit card required.